Media Gallery
Complete collection of cybersecurity projects, labs, and technical demonstrations. Click any image to view details.
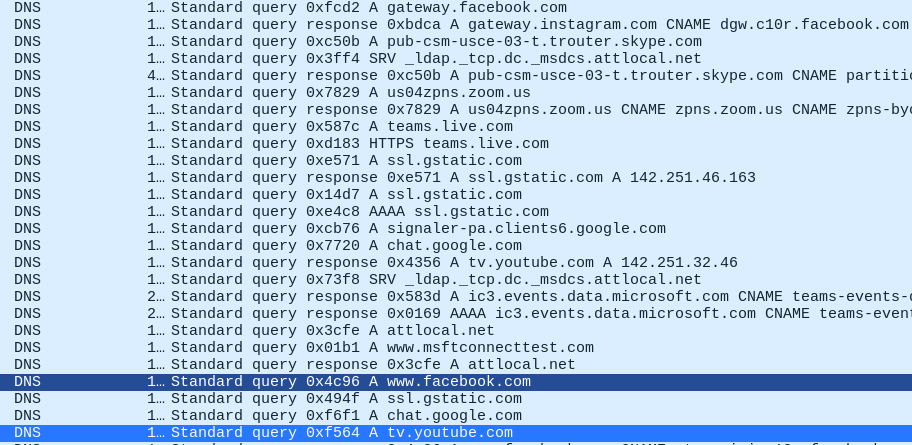
DNS and TLS Traffic Analysis in Wireshark
Packet capture analysis of DNS queries and responses during TLS session monitoring on owned devices.
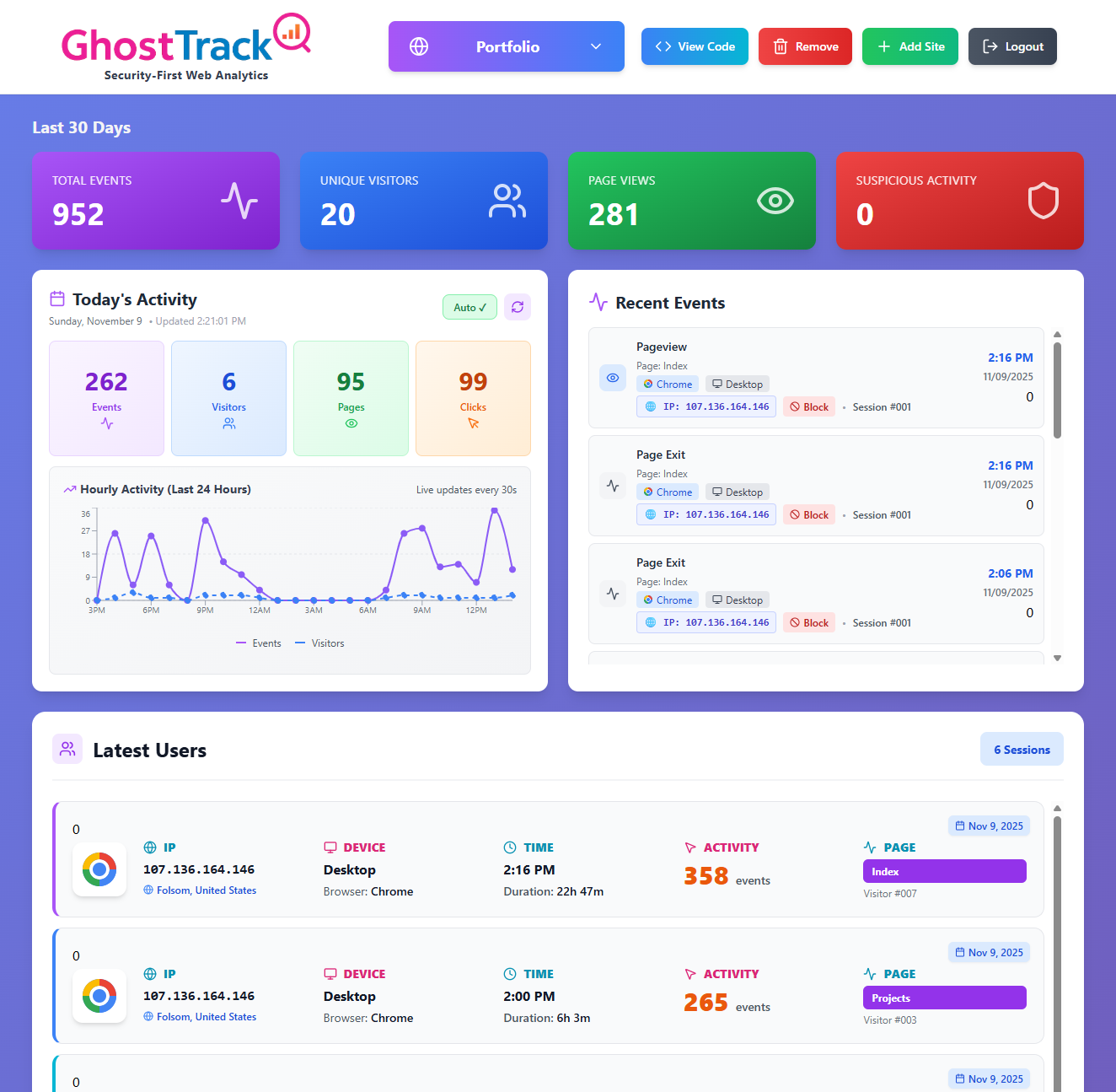
GhostTrack Analytics Live Dashboard Deployment
Production deployment of GhostTrack analytics platform showing real-time visitor tracking, event monitoring, and comprehensive session data across multiple devices and browsers.
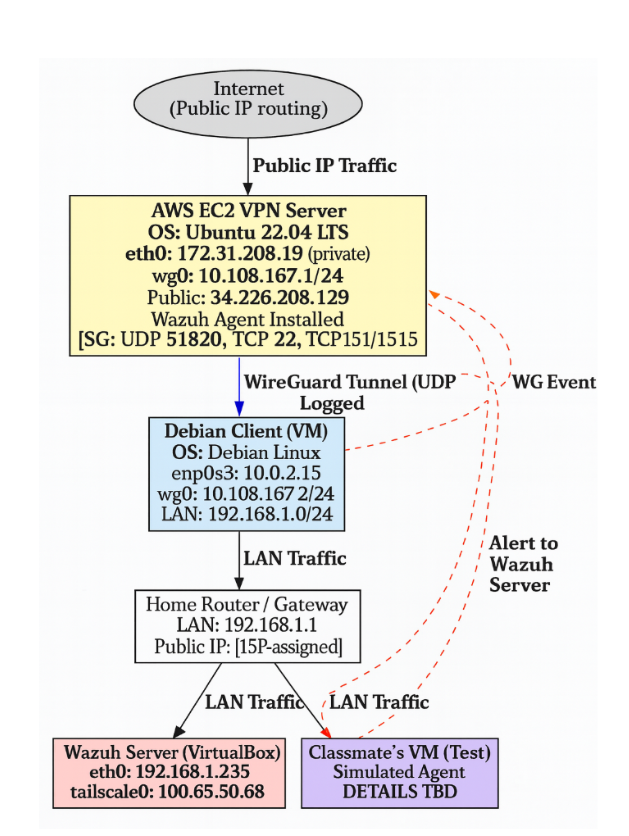
WireGuard VPN Network Architecture
Network topology diagram showing AWS EC2 VPN server with Wazuh SIEM integration and client routing.

CompTIA Security+ Certification
Official CompTIA Security+ certification validating foundational cybersecurity skills in network security, threats, vulnerabilities, and risk management.
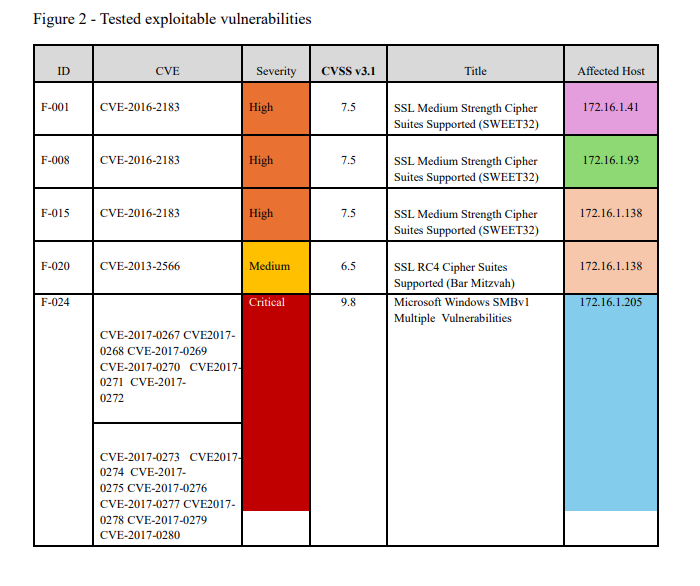
Vulnerability Assessment - Tested Exploits Chart
Comprehensive vulnerability assessment chart from internal penetration testing report. Documents tested exploitable vulnerabilities including CVE-2016-2183 (SWEET32), CVE-2013-2566 (RC4 Cipher), and critical Microsoft Windows SMBv1 vulnerabilities (CVE-2017-0267 through CVE-2017-0280) with CVSS scores and affected hosts.
Web Application Security - CourtCrate Reconnaissance Response
Security incident response documentation for CourtCrate e-commerce application showing detection and mitigation of reconnaissance activity. Report details suspicious IP blocking, threat analysis, and defensive measures implemented to protect the web application infrastructure.
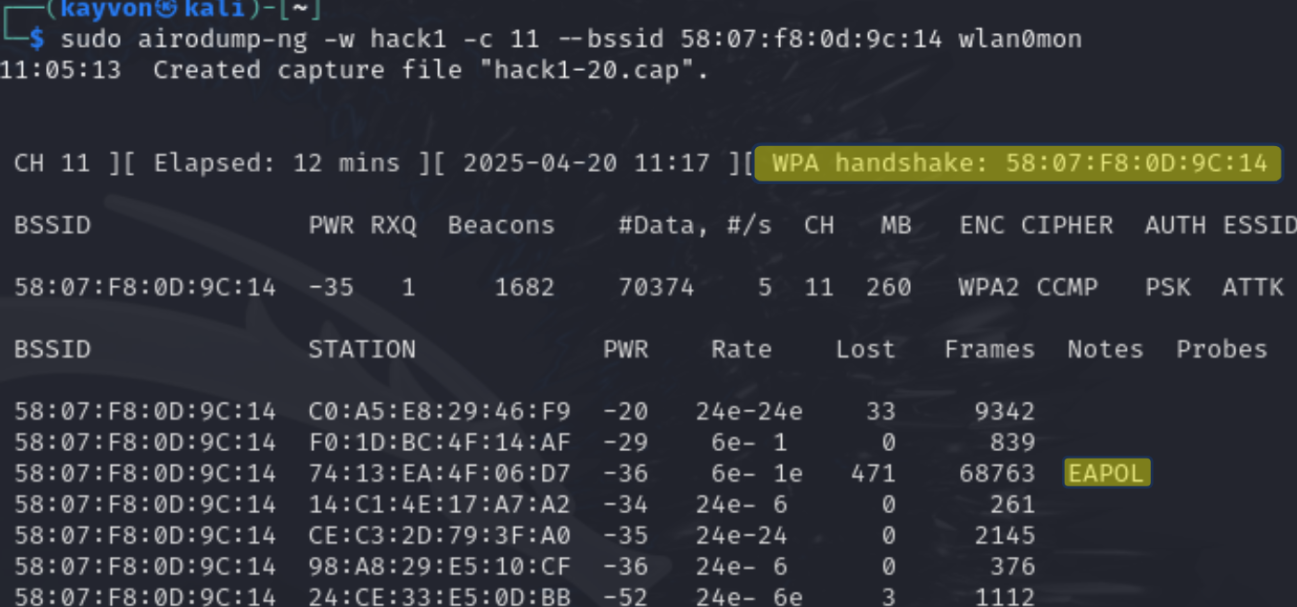
WPA2 Handshake Capture with Airodump-ng
Successful four-way handshake capture on WPA2-PSK network using monitor mode in Kali Linux.
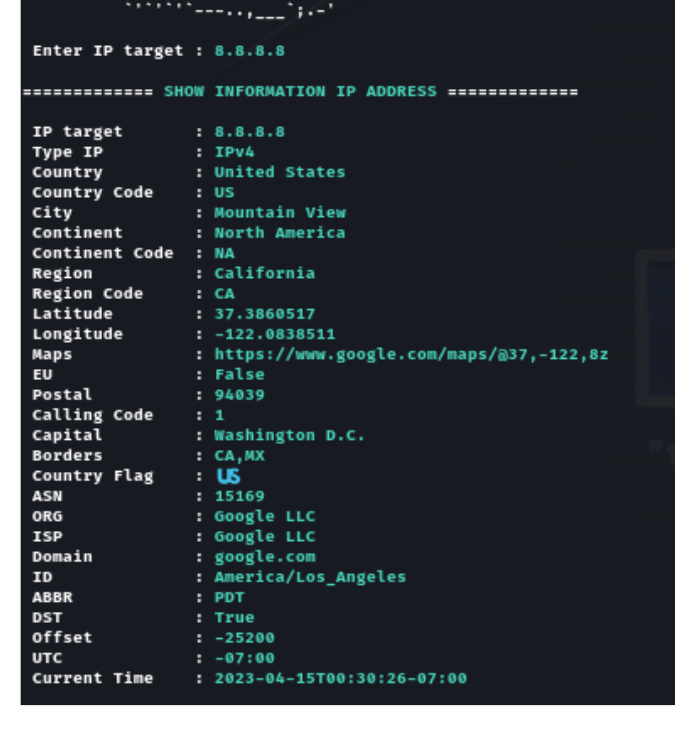
GhostTrack IP Geolocation Lookup Tool
Command-line interface displaying comprehensive IP geolocation data including coordinates, timezone, network information, and organizational details for visitor analysis.
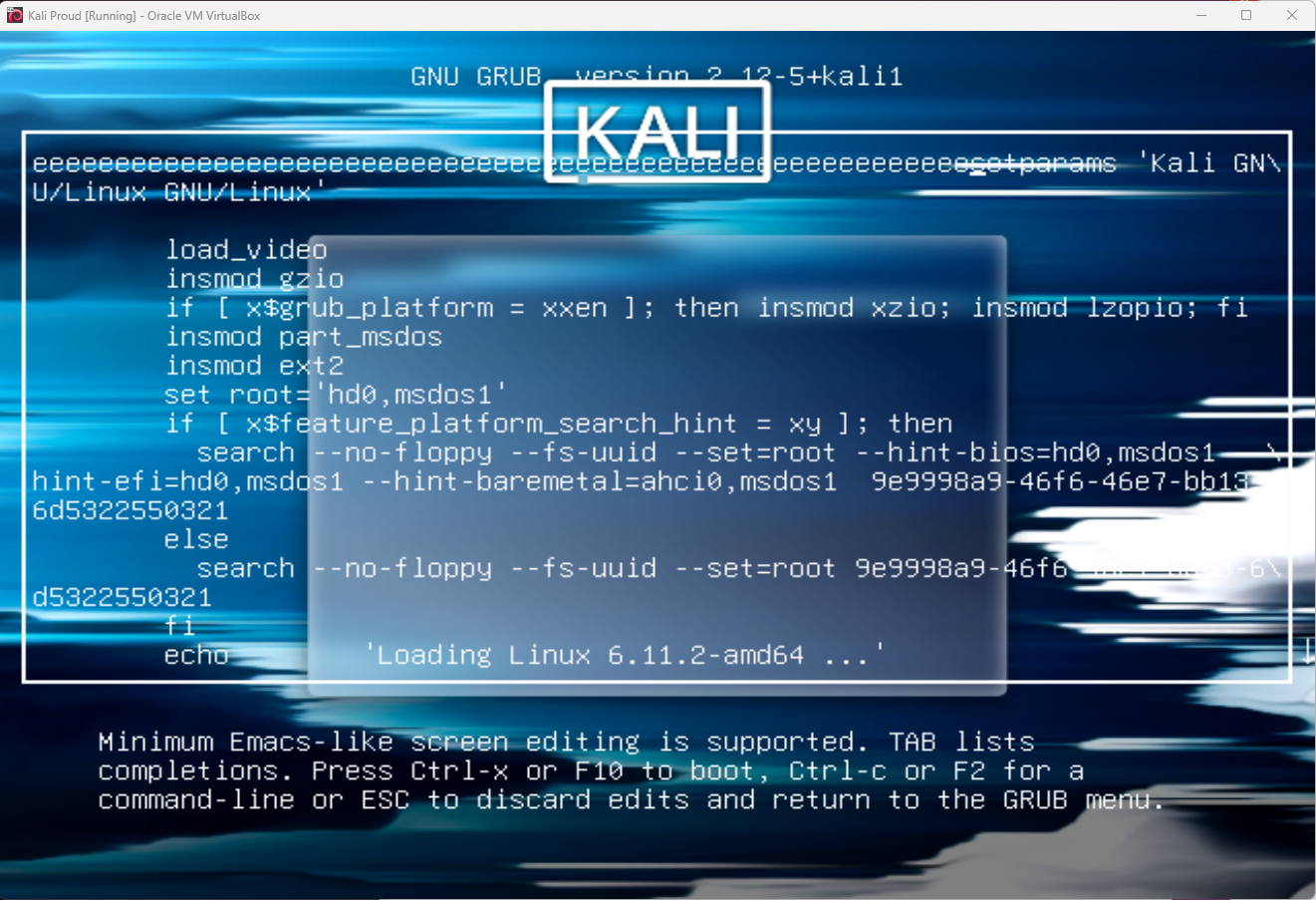
GRUB Bootloader - Bypassing Kali Linux Login
Demonstration of bypassing Kali Linux login authentication by modifying kernel boot parameters through GRUB bootloader menu to gain root access.
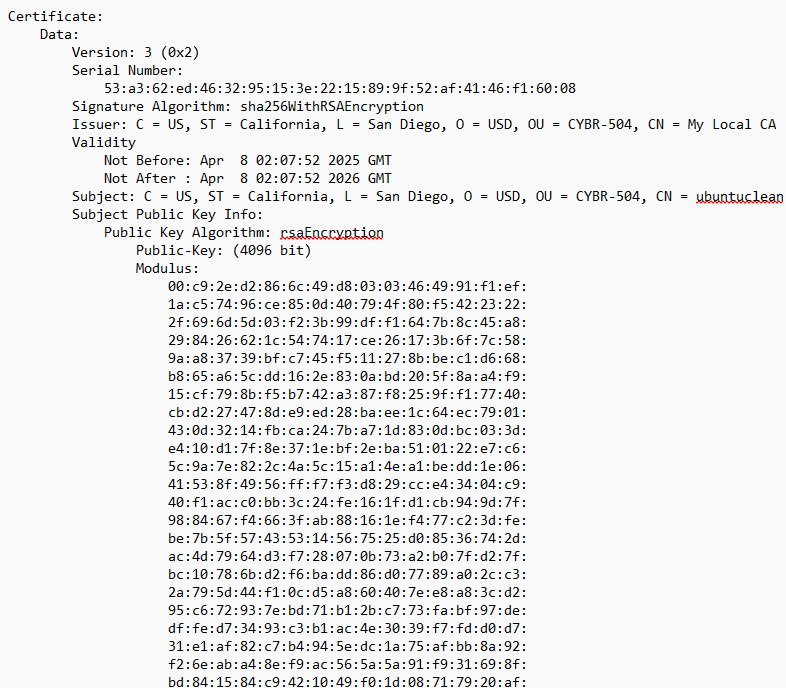
RSA Self-Signed Certificate Generation
Creating SHA256withRSA encrypted certificate with 4096-bit public key for SSL/TLS testing.
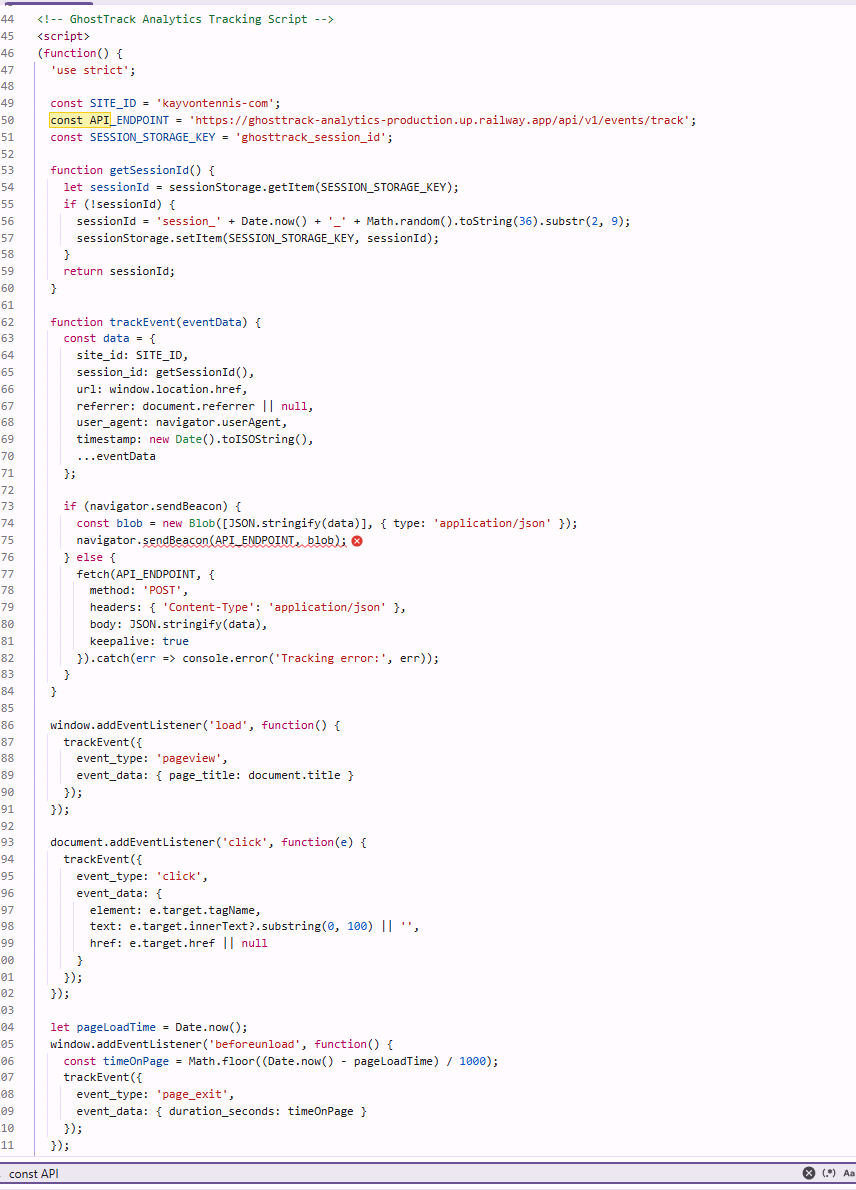
GhostTrack JavaScript Tracking Script Implementation
Client-side tracking script showing session management, event data collection, and API endpoint configuration for real-time analytics aggregation.

Successful WPA2 Key and Wi-Fi Password Cracking
Dictionary attack using Aircrack-ng revealing WPA2 pre-shared key after testing 993,611 keys.
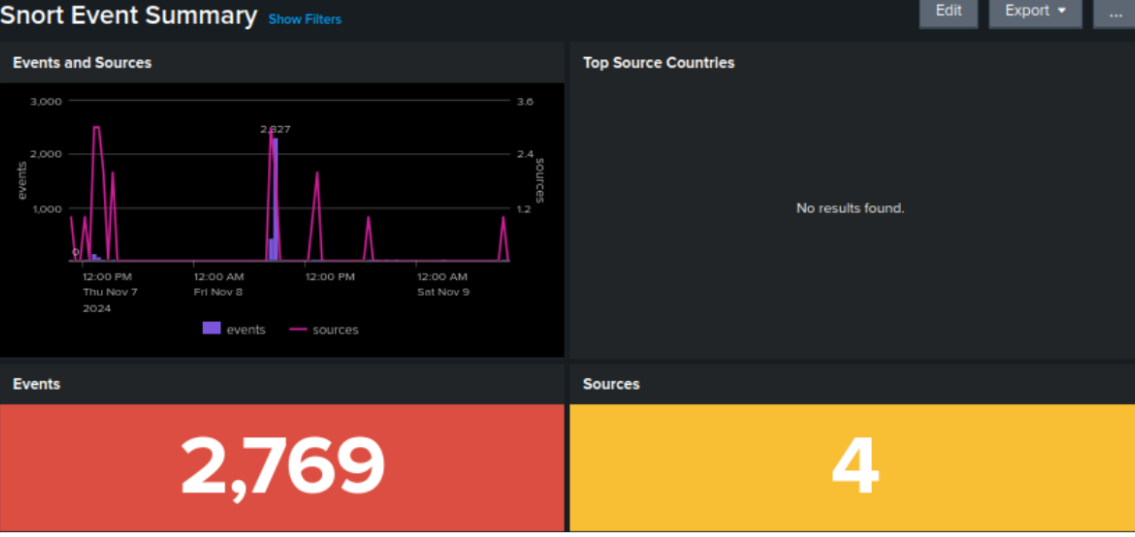
Snort IDS Event Summary Dashboard
Real-time intrusion detection monitoring showing 2,769 security events across 4 source IPs.
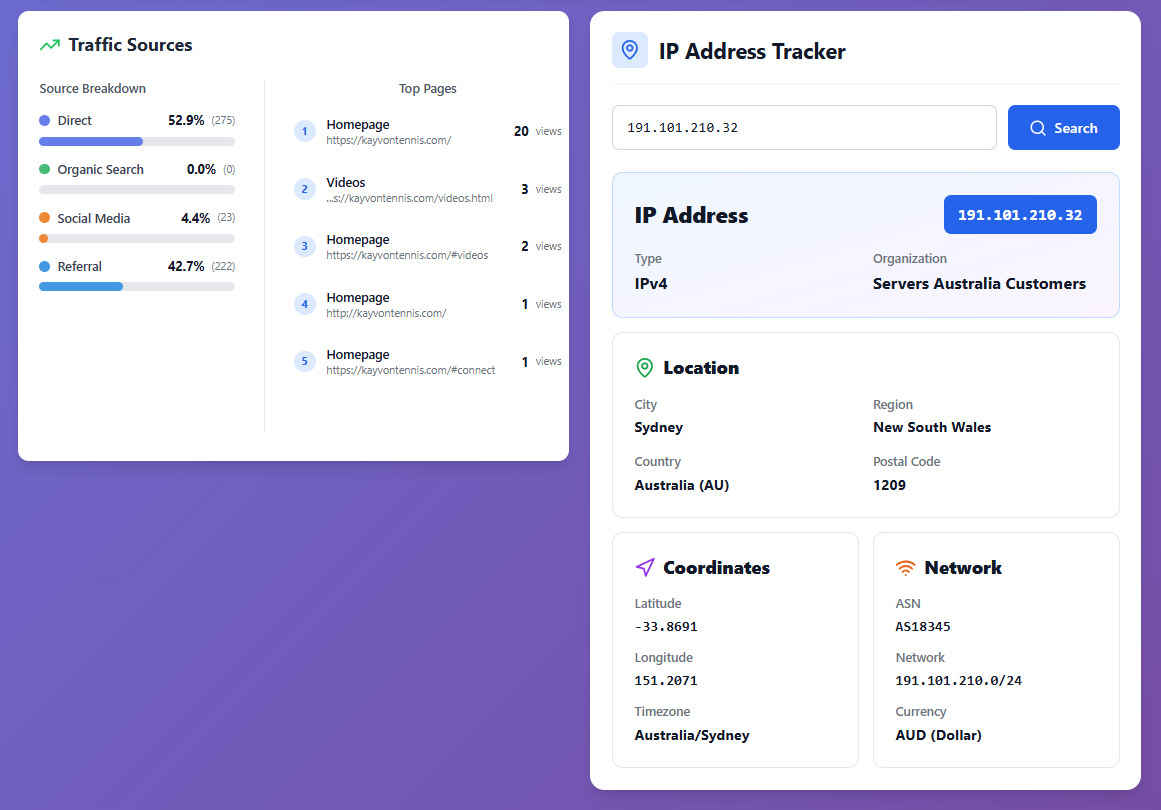
GhostTrack Traffic Sources and IP Address Tracker
Analytics dashboard displaying traffic source breakdown with direct, organic, social media, and referral metrics, alongside detailed IP address geolocation tracking for visitor analysis.
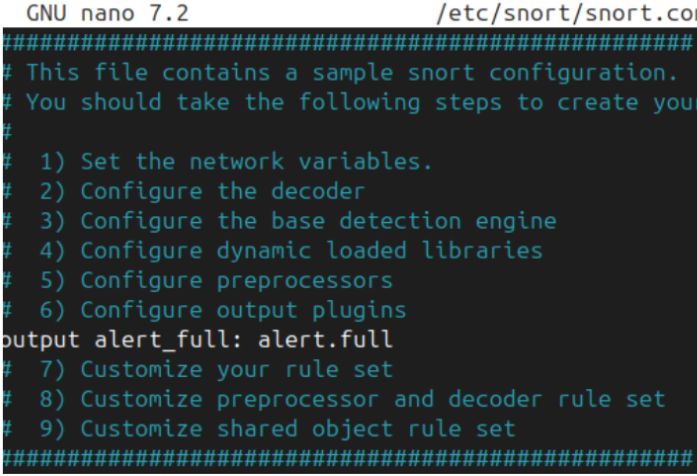
Snort Configuration File Customization
Editing Snort detection engine settings, preprocessors, and output plugins in nano editor.
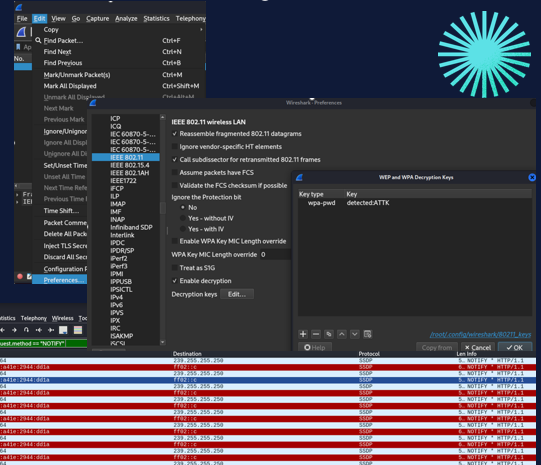
TLS Session Key Pre-Master Secret Setup
Configuring Wireshark with encryption keys to decrypt and analyze HTTPS traffic flows.

GhostTrack Railway Platform Deployment Configuration
Production deployment on Railway platform showing GitHub integration, environment variable configuration, PostgreSQL database connection, and automated CI/CD pipeline for continuous deployment.
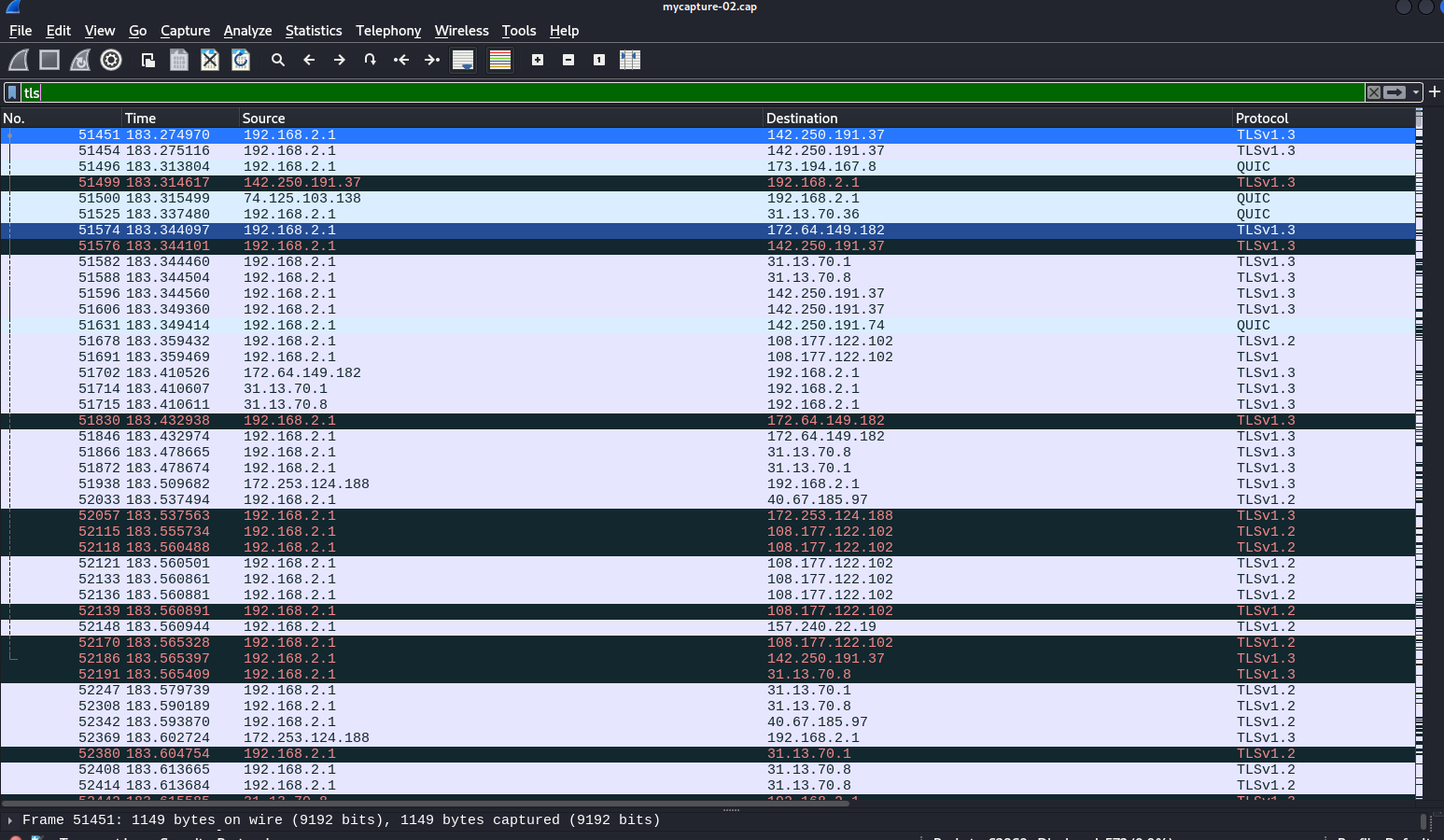
TLS Protocol Traffic Packet Analysis in Wireshark
Deep packet inspection of TLS 1.2/1.3 encrypted sessions showing handshake and data exchange.
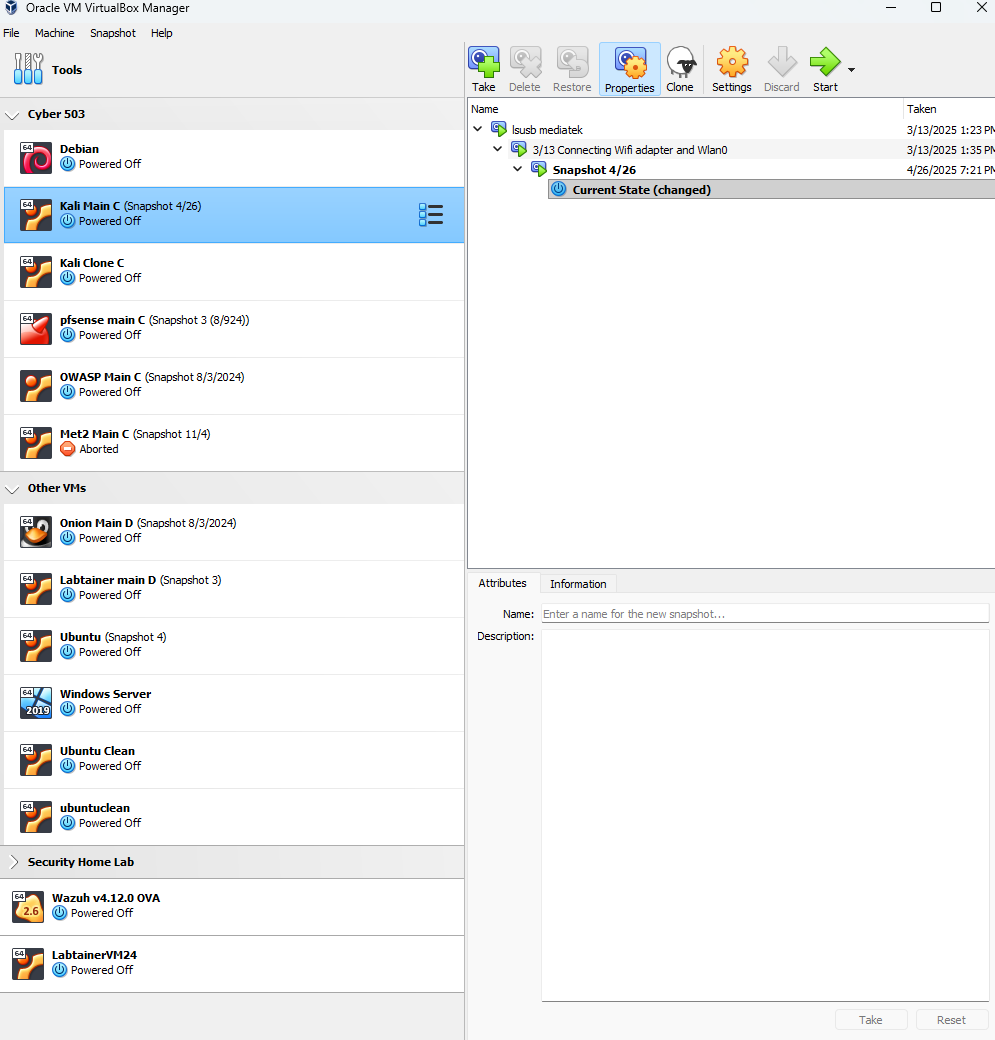
VirtualBox Security Lab Environment
Multi-VM sandbox configuration with Kali, Debian, Ubuntu, and Windows for penetration testing.
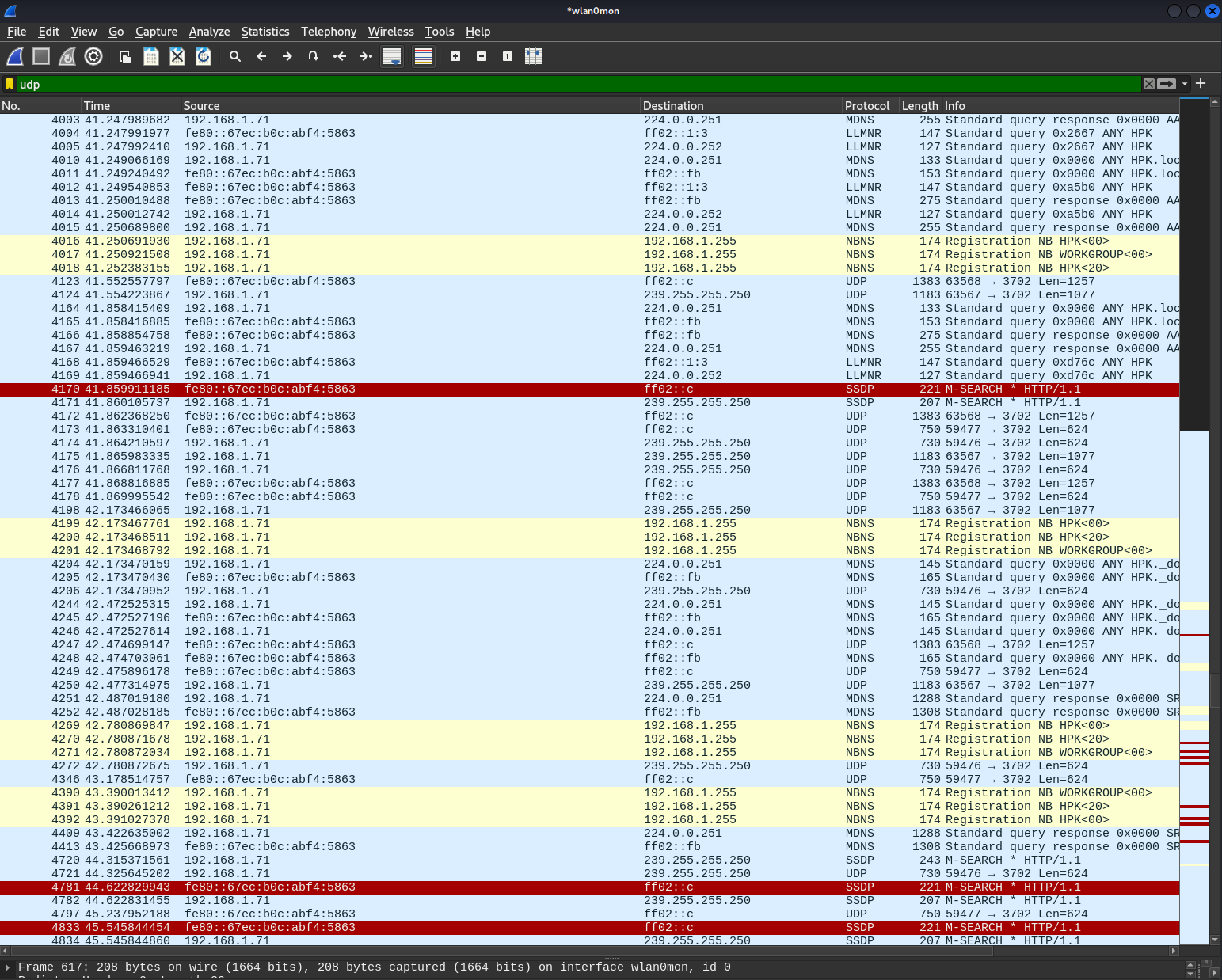
UDP Protocol Network Traffic Capture
Analyzing UDP datagram packets including MDNS, SSDP, and NetBIOS name service broadcasts.

UPnP Device Discovery Protocol Analysis
SSDP multicast packet examination revealing device location and service advertisement data.
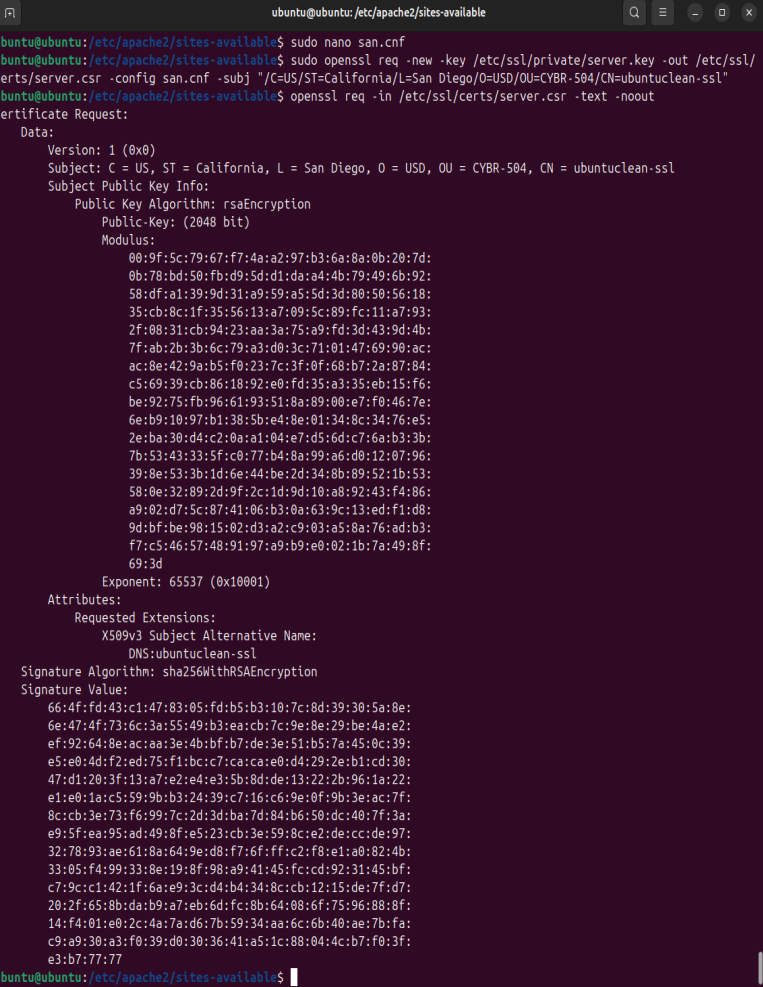
OpenSSL Certificate Signing Request
Generating CSR with RSA encryption and subject alternative name for SSL certificate authority.

Cyber Proud Pre-Apprenticeship Certificate
Official completion certificate for comprehensive cybersecurity training program (May 2025).
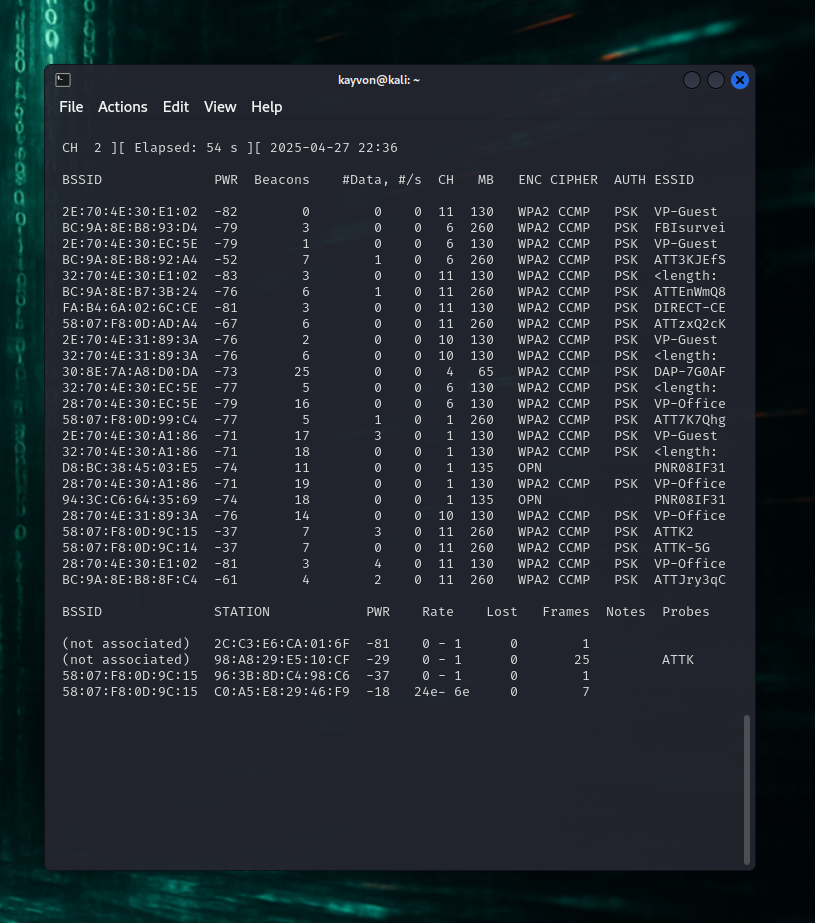
Wireless Network Reconnaissance Scan
Airodump-ng monitoring showing target SSID, connected stations, and WPA2-CCMP encryption details.

USB WiFi Adapter Monitor Mode Setup
VirtualBox USB passthrough configuration enabling packet injection for wireless security testing.
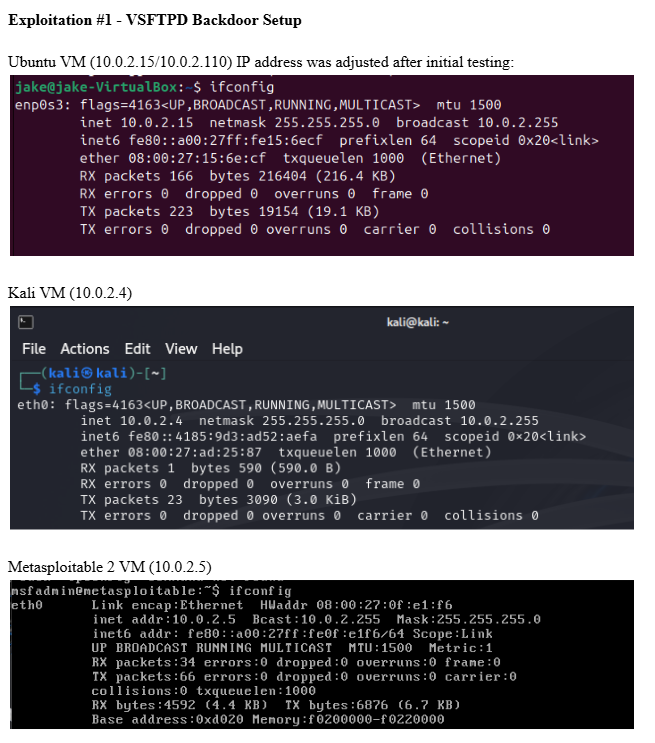
Network Interface Configuration for VSFTPD
VM network setup showing interface addressing for VSFTPD backdoor exploitation assessment.

GhostTrack WordPress Plugin - Admin Dashboard
Custom WordPress plugin for GhostTrack Analytics deployed in WooCommerce admin panel, enabling one-click integration and seamless site tracking configuration.